Key Elements of a Cyber Background Check

Introduction & Importance of Cyber Background Checks
A cyber background check is a thorough process of investigating an individual’s or organization’s digital presence, behavior, and history to assess potential risks related to cybersecurity and online conduct. This type of background check typically involves an evaluation of a person’s online footprint, including their social media activity, online interactions, browsing history, and digital communications, among other aspects. It is also used to identify criminal records, financial risks, and any possible cybersecurity threats associated with the person or entity in question.
In today’s highly digital world, where personal and organizational information is increasingly vulnerable to cyberattacks, cyber background checks have become an essential tool for organizations and individuals who want to ensure that their digital security is not compromised by hiring untrustworthy or high-risk individuals.
Why Individuals and Organizations Conduct Cyber Background Checks
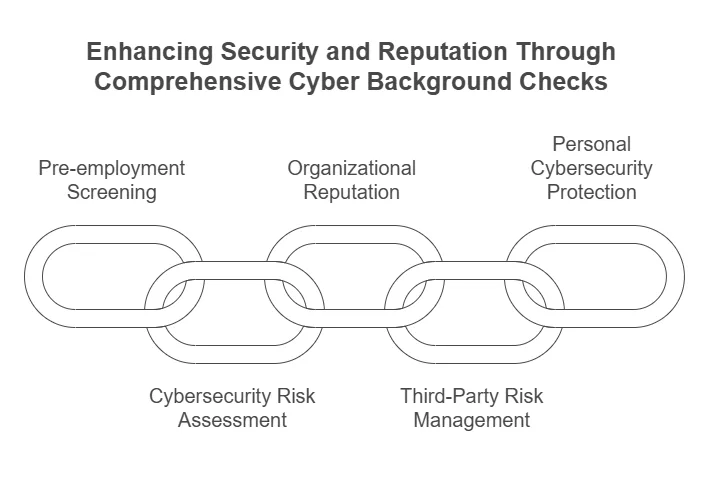
Cyber background checks are essential for individuals, especially those who engage in online business or high-stakes roles, and for organizations that need to safeguard sensitive data, intellectual property, and their online reputation. Here are several key reasons why cyber background checks are conducted:
1. Pre-employment Screening and Risk Mitigation
Before hiring new employees, especially those in critical positions that handle sensitive data or access to internal networks, organizations need to assess the cyber risk posed by these individuals. A cyber background check can uncover any signs of malicious intent, questionable online behavior, or prior involvement in activities such as hacking, fraud, or data breaches. This is particularly important for companies involved in finance, healthcare, or technology where data security is a top priority.
2. Cybersecurity Risk Assessment
In the digital age, an individual’s online presence can reveal potential risks that go beyond traditional criminal background checks. Cybercriminals or individuals with poor cybersecurity hygiene can pose serious threats to an organization. Cyber background checks allow organizations to identify whether an applicant or business partner has been involved in past cybercrimes or is vulnerable to digital attacks due to their online behavior.
3. Protecting Organizational Reputation
Employees, contractors, and affiliates who engage in online misconduct (e.g., inappropriate social media posts, offensive comments, or illegal activities) can damage an organization’s reputation, even if these actions occur outside of the workplace. By conducting thorough cyber background checks, organizations can ensure that those they work with uphold high ethical standards, both online and offline.
4. Contractor & Third-Party Risk Management
Organizations often work with third-party contractors and vendors who have access to sensitive data or systems. Conducting a cyber background check on these external partners is essential to assess the security risks they may pose to the organization.
5. Personal Cybersecurity Protection
Individuals also use cyber background checks to evaluate the trustworthiness of people they engage with online, whether it’s for personal, financial, or business reasons. For instance, before entering into any business deals, entering online communities, or even dating, individuals might want to ensure they are not dealing with cybercriminals, scammers, or fraudsters.
Benefits of Using Cyber Background Checks for Security and Risk Management
Cyber background checks offer a range of benefits for both individuals and organizations when it comes to cybersecurity and risk management. Here’s why they are so important:
1. Enhanced Security
By conducting cyber background checks, businesses and individuals can identify risks that are otherwise invisible during traditional background checks. Risk factors such as involvement in cybercrime, history of data breaches, or illegal online activities can be detected, which helps prevent potential threats from becoming reality.
2. Minimized Cybersecurity Threats
Cyber background checks help to mitigate the chances of hiring employees or partners who may engage in activities like data theft, hacking, or phishing attacks. These checks also help identify individuals who may be more susceptible to external cyber threats due to poor cyber hygiene or vulnerability to manipulation.
3. Informed Decision-Making
Cyber background checks empower employers and individuals to make informed decisions regarding potential hires, business partnerships, and other engagements. Understanding an individual’s digital behavior and history can provide valuable insights into their character, reliability, and overall suitability for roles that require access to sensitive data.
4. Improved Compliance
For organizations operating in regulated industries like banking, finance, or healthcare, performing thorough cyber background checks can help meet compliance requirements. Regulations such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act) mandate that companies take specific steps to protect their data and customer information, making cyber background checks an essential tool for compliance.
5. Reputation Protection
Hiring individuals or engaging with third parties who have questionable online activities or criminal backgrounds could damage the reputation of an organization or individual. Cyber background checks help ensure that the individuals you engage with are not involved in activities that could tarnish your personal or professional reputation.
6. Proactive Risk Management
Cyber background checks allow organizations to identify potential security gaps and vulnerabilities early on. By identifying at-risk individuals during the recruitment or vetting process, businesses can take proactive steps to mitigate cybersecurity threats before they become real problems.
Step-by-Step Guide to Conducting a Cyber Background Check
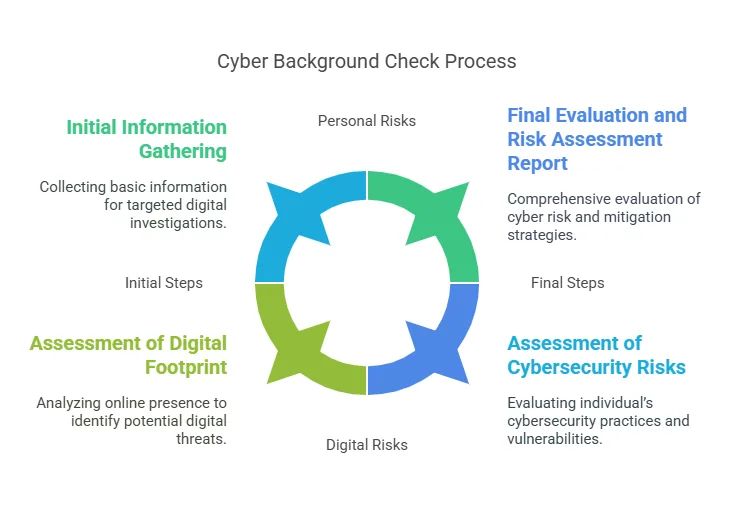
The process of performing a cyber background check can be complex, requiring the use of advanced tools and strategies to dig deep into a person’s or organization’s online presence and digital history. Below is a breakdown of the essential steps involved in conducting a comprehensive cyber background check:
Step 1: Initial Information Gathering
Before diving into detailed investigations, gather the following basic information about the subject of the check:
- Full name
- Date of birth
- Social Security Number (SSN) (if applicable)
- Known aliases or usernames used in social media, gaming, forums, etc.
- Email addresses used by the individual or entity
This basic information allows the background checker to accurately link digital footprints and conduct targeted investigations into specific online activities.
Step 2: Assessment of Digital Footprint
The digital footprint includes any information that an individual has left behind across the internet, whether intentionally or accidentally. This includes:
- Social media profiles (Facebook, Twitter, LinkedIn, Instagram, etc.)
- Blog posts, online articles, and forums
- Comments, reviews, and posts on public websites
- Website ownership (if applicable)
- Online purchases or memberships
By analyzing the digital footprint, a cyber background check can uncover a person’s online behavior, interests, and even potential threats based on the content they’ve shared or engaged with.
Step 3: Review of Criminal Records and Legal Involvement
While criminal background checks typically focus on offline activity, cyber background checks also examine cybercrime involvement. This can include:
- Past involvement in hacking or data theft
- Online fraud or identity theft
- Participation in illegal online activities (e.g., phishing, spamming, cyberbullying, etc.)
- Any involvement in lawsuits related to digital misconduct
Cybercrime databases, law enforcement records, and public legal documents are typically used to identify such issues. For businesses, ensuring that potential hires or partners have no criminal history tied to cyber offenses is vital for maintaining organizational security.
Step 4: Analysis of Social Media Behavior
Social media profiles are rich sources of information that can reveal a lot about an individual’s character and online activity. During the cyber background check process, the following aspects are examined:
- Posts, comments, and likes – Reviewing the content an individual interacts with, and whether their posts reflect any risky behaviors.
- Connections and associations – Identifying connections with high-risk individuals or groups that could pose a threat.
- Online reputation – Checking how the individual is perceived by their followers, and looking for any red flags like inflammatory remarks, controversial opinions, or hostile interactions.
Step 5: Financial History and Risk Assessment
Understanding an individual’s financial behavior is a critical component of the cyber background check process. The financial history helps reveal if the individual is prone to financial distress, which could expose an organization to risks, such as:
- Financial instability – Individuals in financial trouble may be more likely to engage in fraud or other criminal activities.
- Bankruptcy filings or overdue debts – These may be indicators of potential vulnerability to external manipulation or poor decision-making.
- Transaction records and credit history – A review of an individual’s financial history can reveal inconsistencies or potential threats.
This information is typically gathered through credit reporting services and financial databases that allow background checkers to access data regarding an individual’s financial standing.
Step 6: Assessment of Cybersecurity Risks
As cybersecurity becomes a primary concern for organizations, cyber background checks also assess an individual’s susceptibility to cyberattacks or security risks. This includes:
- Security hygiene – Does the individual follow basic security protocols, such as using strong passwords, enabling two-factor authentication, or regularly updating their software?
- Previous security incidents – Has the person been involved in a data breach, compromised their own security, or shown vulnerabilities that may put organizational systems at risk?
- Engagement in risky online behaviors – This includes accessing untrusted websites, downloading questionable files, or engaging in phishing attempts.
These checks can be conducted by examining network activities or utilizing specialized cybersecurity tools that assess risk.
Step 7: Review of Publicly Available Data
In many cases, there is publicly available data that can provide insight into an individual’s or organization’s online behavior. This may include:
- Public records such as court rulings, bankruptcy filings, or government actions.
- Press mentions or news articles that could indicate involvement in scandals or controversial activities.
- Professional licensing information from regulatory bodies, which helps to verify claims of professional credentials.
Checking publicly available data adds an extra layer of transparency to the cyber background check process.
Step 8: Final Evaluation and Risk Assessment Report
After gathering all necessary data, a comprehensive evaluation is conducted to assess the overall cyber risk posed by the individual or organization. This final report includes:
- Risk level – A determination of whether the individual poses any cybersecurity threats.
- Recommendations – Suggestions for mitigating the risk, which could include monitoring the individual’s online activities, implementing additional security protocols, or avoiding engagement altogether.
- Red flags – Any behaviors or activities that stand out as major concerns.
Key Components of a Cyber Background Check
Now that we’ve outlined the steps involved in conducting a cyber background check, let’s focus on the key components that are typically analyzed in the process. These are the critical areas where cyber risks and vulnerabilities are often found:
- Online Footprint & Digital Presence – As mentioned earlier, a person’s digital footprint is a reflection of their online identity. A thorough review includes social media profiles, online activities, and any digital trace they leave behind.
- Criminal History & Cybercrime Records – Checking for any involvement in online fraud, hacking, or other illegal digital activities.
- Social Media Analysis – A deep dive into the individual’s interactions on social media platforms, looking for inappropriate or risky behavior.
- Financial History – Assessing financial stability, including outstanding debts, bankruptcies, and any history of fraudulent financial activities.
- Cybersecurity Risks – This focuses on evaluating an individual’s online security practices, including whether they are susceptible to cyberattacks or have been involved in past cybersecurity incidents.
- Public Records & Legal History – Any available legal records or press coverage that could impact the individual’s reputation and perceived trustworthiness.
Precise Hire’s Cyber Background Check Services
At Precise Hire, we specialize in providing comprehensive cyber background checks to help businesses and individuals make well-informed decisions about their digital security and partnerships. Our services cover everything from evaluating social media behavior to analyzing financial history and cybersecurity risks.
By leveraging our advanced tools and professional expertise, we ensure that your cyber risk assessment is thorough, accurate, and aligned with your security requirements.
Legal Considerations Related to Cyber Background Checks
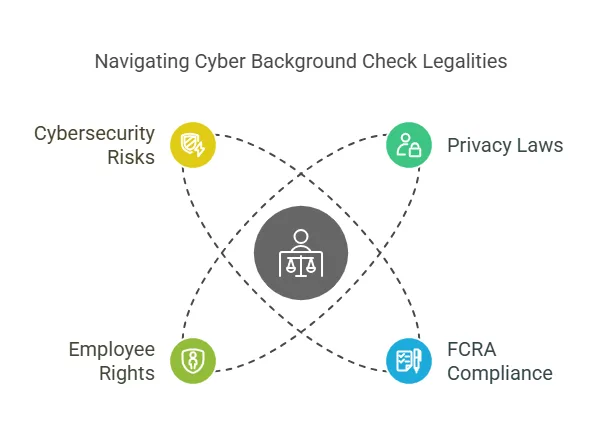
When conducting a cyber background check, it’s crucial to be aware of the various legal implications to ensure that the process is compliant with relevant privacy laws, data protection regulations, and employee rights. Failing to adhere to these legal standards can result in significant legal issues, financial penalties, and reputational damage for the organization conducting the background check. Below are the key legal considerations that need to be addressed:
1. Privacy Laws and Data Protection Regulations
Data privacy laws govern how personal information is collected, processed, and shared, and these laws play a critical role in cyber background checks. Depending on the jurisdiction, organizations must comply with specific regulations to ensure that they are handling sensitive data responsibly.
- General Data Protection Regulation (GDPR): If the subject of the cyber background check is located in the European Union (EU) or if your organization handles the personal data of EU citizens, compliance with the GDPR is mandatory. The GDPR requires that organizations obtain explicit consent from individuals before conducting background checks and that they store and process personal data securely.
- California Consumer Privacy Act (CCPA): This legislation, which applies to residents of California, provides individuals with rights over their personal data, including the right to access, delete, and opt out of the sale of their data. Businesses conducting cyber background checks must adhere to these requirements.
- Health Insurance Portability and Accountability Act (HIPAA): For organizations in the healthcare sector, HIPAA requires that personal health information (PHI) be kept confidential and protected during background checks. Organizations must ensure that they do not breach these rules during the cyber background check process.
These laws also emphasize the need for explicit consent, the protection of sensitive data, and compliance with data retention policies to avoid violations.
2. Fair Credit Reporting Act (FCRA) Compliance
The Fair Credit Reporting Act (FCRA) is a U.S. federal law that regulates how employers, landlords, and other organizations use consumer information in background checks, including those related to financial history and online activities. Under the FCRA, organizations must adhere to the following guidelines:
- Disclosures and Consent: Organizations must inform individuals that a background check will be conducted and obtain written consent before proceeding.
- Adverse Action: If a cyber background check reveals negative information that leads to an adverse decision (such as rejecting a job applicant or terminating a business relationship), the individual must be notified. They also have the right to dispute any inaccuracies in the report.
Non-compliance with the FCRA can lead to legal challenges, including lawsuits, penalties, and damage to an organization’s reputation.
3. Employee Rights and Consent
Employees and job candidates have certain rights when it comes to background checks, including the right to know how their data is being used and to challenge the results if necessary. It’s important that businesses maintain transparency with their employees and obtain informed consent before conducting any cyber background checks.
- Job Applicants: Before conducting a cyber background check on a job candidate, employers must provide them with written consent. Failure to do so can lead to violations of both FCRA and state-specific privacy laws.
- Employee Monitoring: If an organization decides to monitor employees’ digital activities (e.g., emails, internet usage), they must ensure they comply with state and federal laws regarding workplace privacy. In many jurisdictions, employees must be informed of monitoring policies and may have the right to opt out.
4. Cybersecurity Risk and Breach Liability
In some cases, organizations that conduct cyber background checks may be held liable for failing to identify cybersecurity risks or vulnerabilities in an individual’s digital behavior, especially if the individual is later involved in a cyberattack or data breach. This risk is heightened if an organization hires an individual who has been previously involved in cybercrime, data theft, or other activities that compromise cybersecurity.
Organizations should ensure that they assess cybersecurity risks thoroughly during the background check process and follow up with proper security protocols to prevent breaches.
Frequently Asked Questions (FAQs)
Here are some of the most common questions people have about cyber background checks, along with detailed answers:
What is included in a cyber background check?
A cyber background check typically includes an analysis of an individual’s online footprint, including their social media activity, criminal records, financial history, cybersecurity practices, and involvement in any cybercrimes. It can also review publicly available data, such as court records or media mentions, and assess the person’s cybersecurity hygiene.
Why should I conduct a cyber background check?
Conducting a cyber background check helps mitigate cybersecurity risks and protect your organization from potential threats. It can identify individuals involved in cybercrime, fraud, or risky online behaviors that could jeopardize your digital security, reputation, or financial stability.
Is a cyber background check legal?
Yes, cyber background checks are legal when they comply with privacy laws such as the FCRA, GDPR, and CCPA. However, organizations must obtain written consent from the individual being checked and ensure that the data is processed and stored securely to avoid legal repercussions.
How can I ensure my cyber background check is compliant with laws?
To ensure legal compliance, always obtain explicit consent from individuals before conducting a cyber background check. Follow all data protection regulations (such as GDPR or FCRA) and provide transparency about how the collected data will be used. It’s also essential to give individuals an opportunity to dispute any negative findings and rectify inaccuracies.
Can a cyber background check detect a person’s involvement in hacking or cybercrime?
Yes, a comprehensive cyber background check will investigate an individual’s criminal records, cybercrime involvement, and online activities. This may include identifying participation in hacking, fraudulent activities, or other illegal online behaviors. If an individual has a history of cybercrime, this will typically be flagged in the check.
What is included in a cyber background check?
A cyber background check typically includes an analysis of an individual’s online footprint, including their social media activity, criminal records, financial history, cybersecurity practices, and involvement in any cybercrimes. It can also review publicly available data, such as court records or media mentions, and assess the person’s cybersecurity hygiene.
Why should I conduct a cyber background check?
Conducting a cyber background check helps mitigate cybersecurity risks and protect your organization from potential threats. It can identify individuals involved in cybercrime, fraud, or risky online behaviors that could jeopardize your digital security, reputation, or financial stability.
Is a cyber background check legal?
Yes, cyber background checks are legal when they comply with privacy laws such as the FCRA, GDPR, and CCPA. However, organizations must obtain written consent from the individual being checked and ensure that the data is processed and stored securely to avoid legal repercussions.
How can I ensure my cyber background check is compliant with laws?
To ensure legal compliance, always obtain explicit consent from individuals before conducting a cyber background check. Follow all data protection regulations (such as GDPR or FCRA) and provide transparency about how the collected data will be used. It’s also essential to give individuals an opportunity to dispute any negative findings and rectify inaccuracies.
Can a cyber background check detect a person’s involvement in hacking or cybercrime?
Yes, a comprehensive cyber background check will investigate an individual’s criminal records, cybercrime involvement, and online activities. This may include identifying participation in hacking, fraudulent activities, or other illegal online behaviors. If an individual has a history of cybercrime, this will typically be flagged in the check.
Conclusion: The Importance of Thorough Cyber Background Checks
In today’s digital world, where cybercrime and online threats are rampant, conducting thorough cyber background checks is essential for both individuals and organizations. These checks provide a deeper understanding of an individual’s digital behavior, helping to identify potential risks and vulnerabilities that could jeopardize cybersecurity and reputation.
Whether you are hiring new employees, entering into business partnerships, or assessing personal safety, a cyber background check offers invaluable insights into an individual’s online presence, helping to mitigate the risk of cyberattacks, fraud, and security breaches.
By conducting cyber background checks in a legal and responsible manner, you can protect yourself, your organization, and your customers from the growing threat of digital risks. At Precise Hire, we offer comprehensive cyber background check services tailored to meet your needs, ensuring that you have all the information necessary to make secure and informed decisions.
